Authy OneTouch Now On Desktop
The Future Of Authentication
Most authentication across the web is reliant on a username and password pair, a security strategy that’s decades old and out of date. Two-factor authentication (2FA) has helped increase security, but most often it’s implemented by sending security codes via an ever increasingly insecure SMS platform. More and more we see these traditional methods prone to attack and, in response, the industry has been creating better, more modern solutions. Authy’s OneTouch is one such example; it uses push technology to secure the link between your user and your application, in real time, as they are logging in.
Although push technology is nothing new, it’s just beginning to see common use in the authentication space, with the technology industry deploying OneTouch-type approaches in several business and consumer applications, including:
- Yahoo Account Key
- Google Prompt
- Microsoft Authenticator
- SalesForce Lightning Login
- Blizzard Battle.net authenticator
So What’s New For OneTouch?
Authy OneTouch is ideal for mobile users. And while it’s increasingly becoming a mobile world, we are well aware that many users still log into accounts from a desktop or laptop, especially in the workplace.
Until now, OneTouch has primarily been available to iOS and Android users in the free Authy app or embedded directly into existing mobile apps using our SDK. So as of today, we’re adding the convenience of Authy OneTouch to our Authy for desktop application.
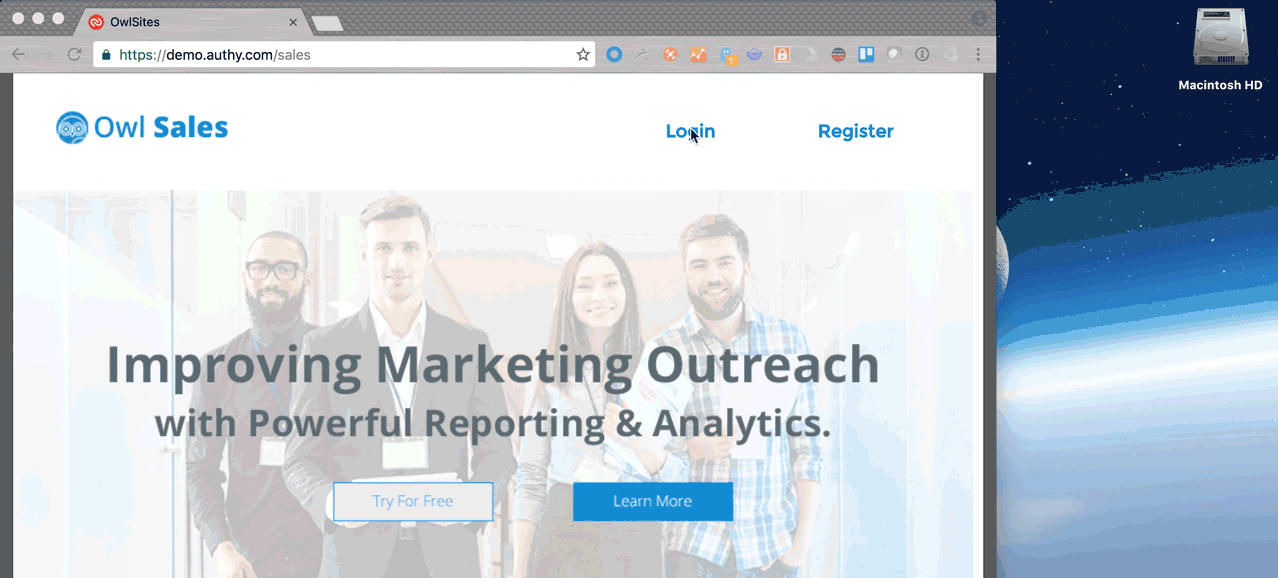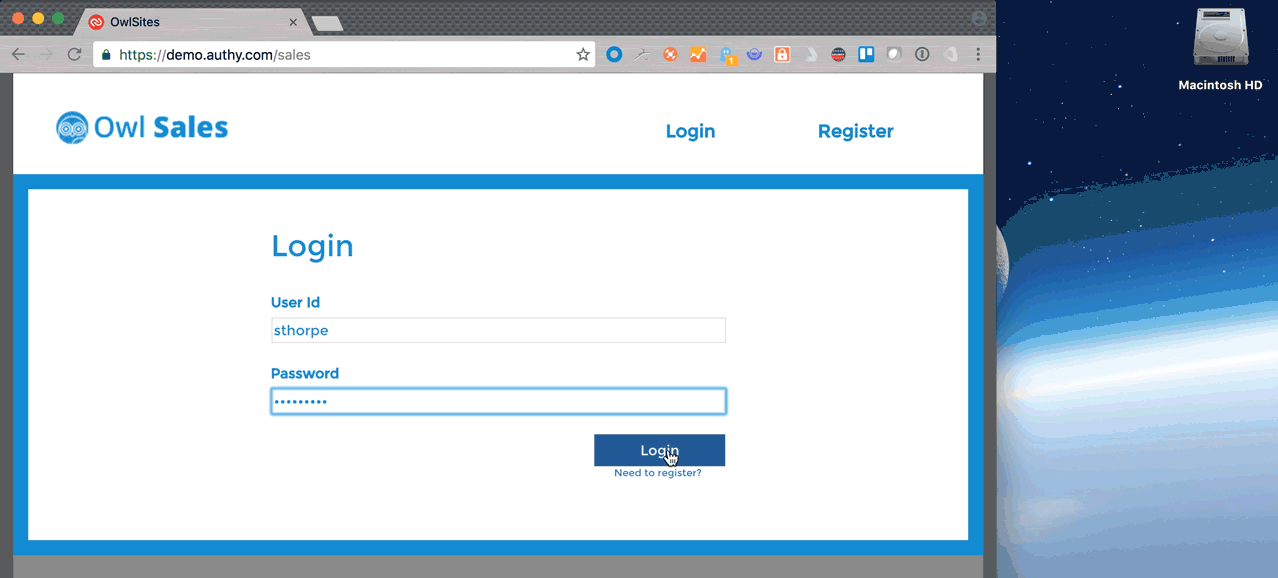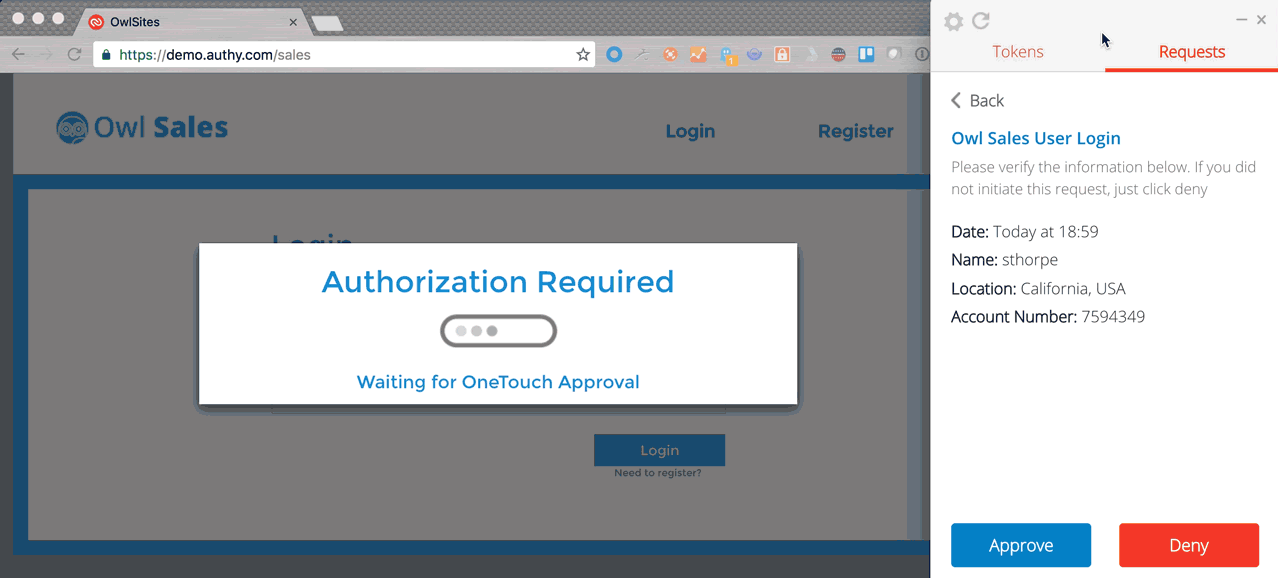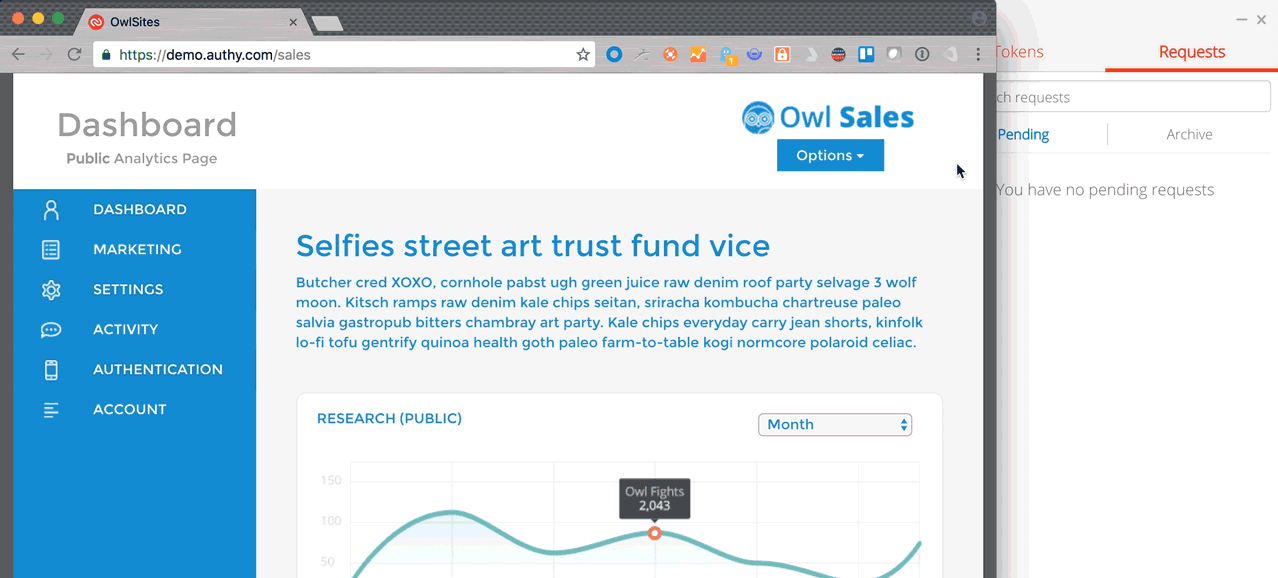
For developers, this means you can deliver notifications directly on your user’s desktops (similar to Facebook and LinkedIn notifications) that will alert you to a pending authentication or authorization request. Clicking on the notification will launch Authy for Desktop and allow you to respond directly from the desktop or laptop. Quicker and more convenient for users, and a whole lot easier for developers.
No Longer Just For 2FA
OneTouch, and other services like it, are typically used for the initial login, where the first factor of authentication (a user entering a username and password) combines with a second factor (push notification to a mobile device). However, with OneTouch, you can now consider removing the password altogether. Yahoo Account Key does exactly this. Once you’ve registered your device (typically a smartphone) you no longer need a password to access your account.
Some of our customers even go beyond the login and implement this new authentication method to secure in application high-value events or risky data changes, such as transferring funds or deleting user accounts.
Today, the traditional method for approving such activities is to communicate by email. For example, in business, a project team may create a purchase order online, and the system shoots out an email to the CFO asking him/her to approve. The CFO will open the email, click on a link, and log in to the application. Once past the standard authentication steps, they must then navigate to the purchase order in question and approve or deny it.
That’s a lot of work, and all those steps (not to mention crowded inboxes) can cause long delays and jeopardize project deliverables. Instead, OneTouch takes this process and reigns it in by sending a quick notification to the decision maker’s phone. Open the app, read the request, review and approve.
Implement Better Authentication
Try Authy OneTouch. Just a few lines of code and a few minutes of your time make it worth investigating. And because it’s now available on the Authy for Desktop, it’s even more convenient than ever. Get started now.
